Data breaches and hacking incidents are no longer something that occurs elsewhere.
2019 saw several major incidents occur in Australia, from the malware attack on Parliament House in January to the spearphishing attack on ANU announced by the Vice-Chancellor in June and the subject of a detailed report later in the year , the phishing attack on PayID users in August to the ransomware attack on Victorian hospitals in September.
In addition to major incidents, 2019 also saw thousands of successful hacking attempts against Australian individuals, businesses and government agencies. The Australian Cyber Security Centre (ACSC) now receives one cybercrime report every ten minutes.
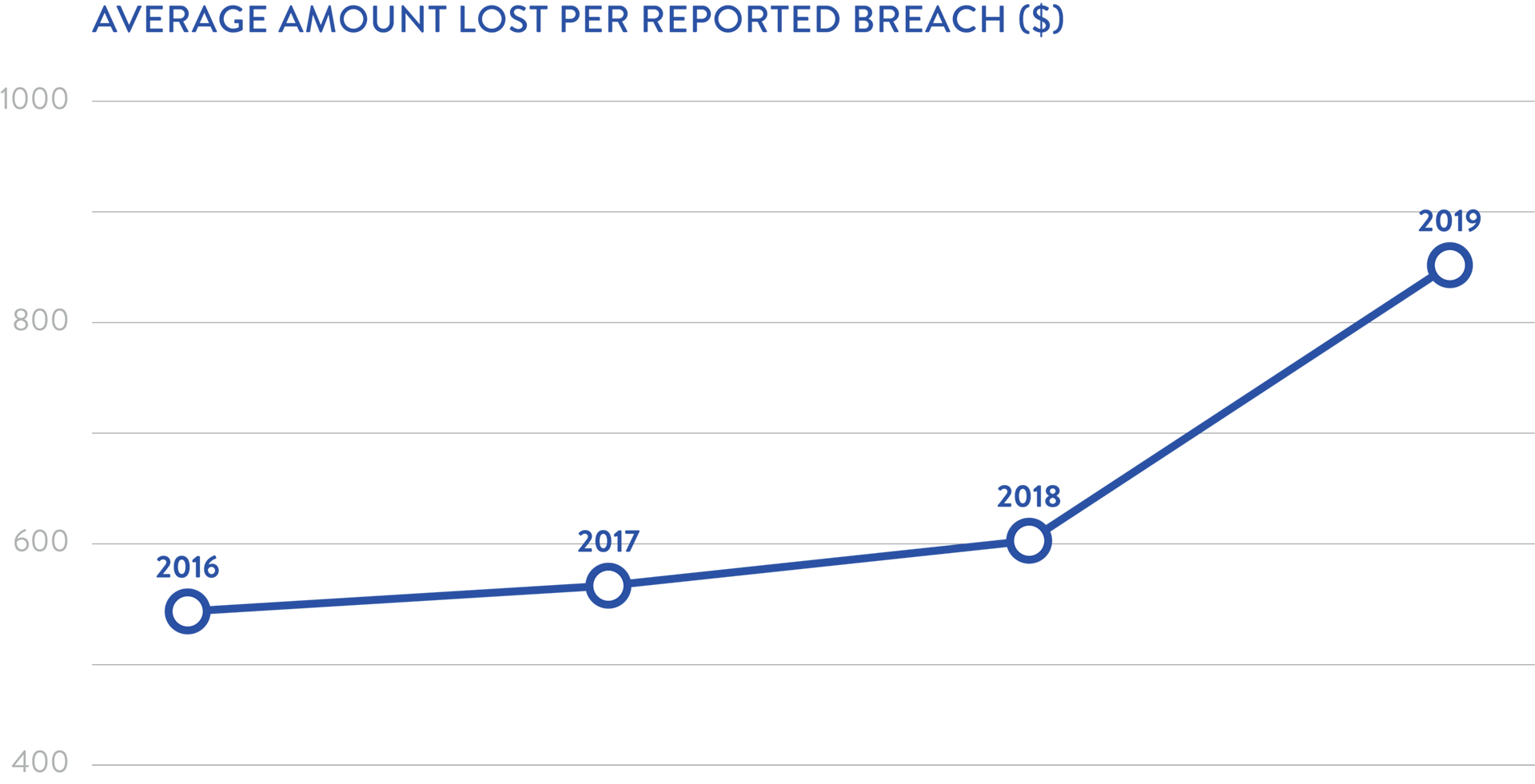
2019 also showed significant growth in the average amount of money lost per reported breach.
Scamwatch identified that prior to December 2019 just over $129M was lost due to cybercrime across the 160,000 reports it received .
Preparation is key
All of this means that individuals, businesses and governments must be more prepared than ever. How can Australian organisations and government agencies prepare for a hack in 2020?
Implementing (and ensuring any IT suppliers are required to implement) robust preventative IT security systems and controls is critical. As evidenced by many of the examples of data breaches in 2019, so too is running regular proactive education and training programs to teach both staff and customers about how to recognise phishing attempts, password management and other physical security measures.
Having a robust data breach response plan in place is also vital. The Office of the Australian Information Commissioner (OAIC) has published guidance on preparing for and responding to data breaches . The OAIC guidance and best practice require clear lines of communication within an organisation and the establishment of a response team (which may include internal and external SMEs) to quickly deal with actual or suspected data breaches.
Know your notification obligations
The plan should document the organisations notification obligations requirements which may arise following an actual or suspected data breach. These may include the following:
Any requirements to notify of actual or suspected data breaches which arise under contracts with third parties, such as customers, service providers or insurers.
In addition to requiring IT suppliers to implement appropriate IT security measures, business and government agencies should also ensure any IT contracts enable compliance with any legally required data breach notification requirements. See our previous insights on ensuring contracts are compliant with data breach notification laws .